GuardianKey fits your business!
The challenge
Educational organizations deal with data related to the academic life of students, and personal and research information, which require protection. The relevance of educational organizations makes them golden targets for hacktivism and crackers. The business depends on the organization's reputation. Unauthorized accesses may cause data leaks and trigger relevant reputation and financial losses.
Protect against attacks
Brute force
Account takeover
Automated attacks
Anonymization
Credential stuffing
Password guessing
The solution
GuardianKey Auth Security provides an intelligent approach to protect the authentication in your systems and services. It requires minor changes and is frictionless. Your Stronger Authentication!
How GuardianKey works
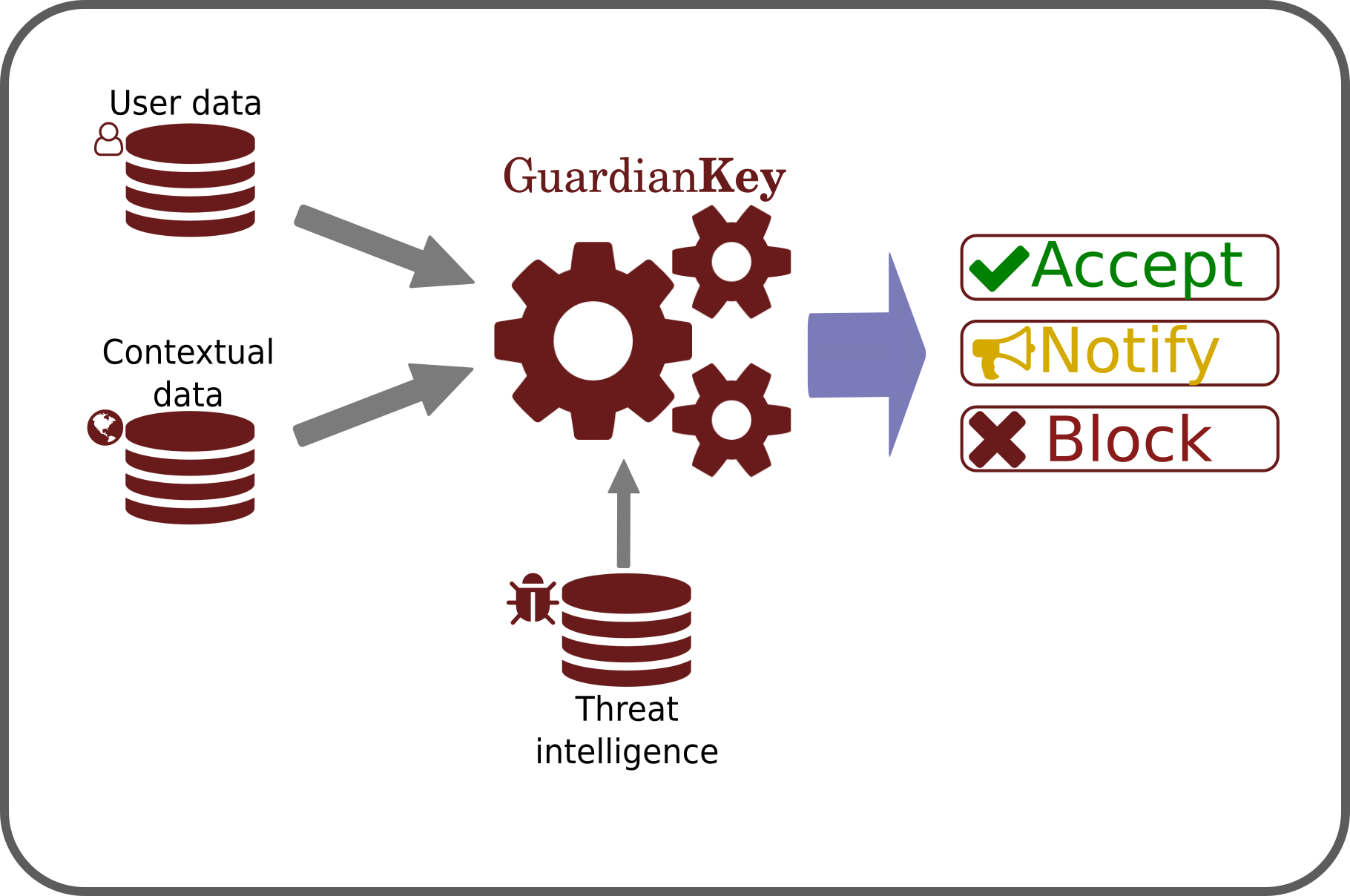
The detection engine uses Machine Learning and our secret mathematical risk formula to combine the following three analysis approaches:
-
Threat Intelligence
-
Behavioral Profiling
-
Psychometric Profiling (or Behavioral Biometrics Profiling)¹
Using these three pillars, our engine computes a risk for each event sent by the protected systems.
In real time, the online attempt can be blocked, an extra requirement can be requested to the user, or notifications can be triggered.
¹ Currently available only for our Android SDK.
GuardianKey in action
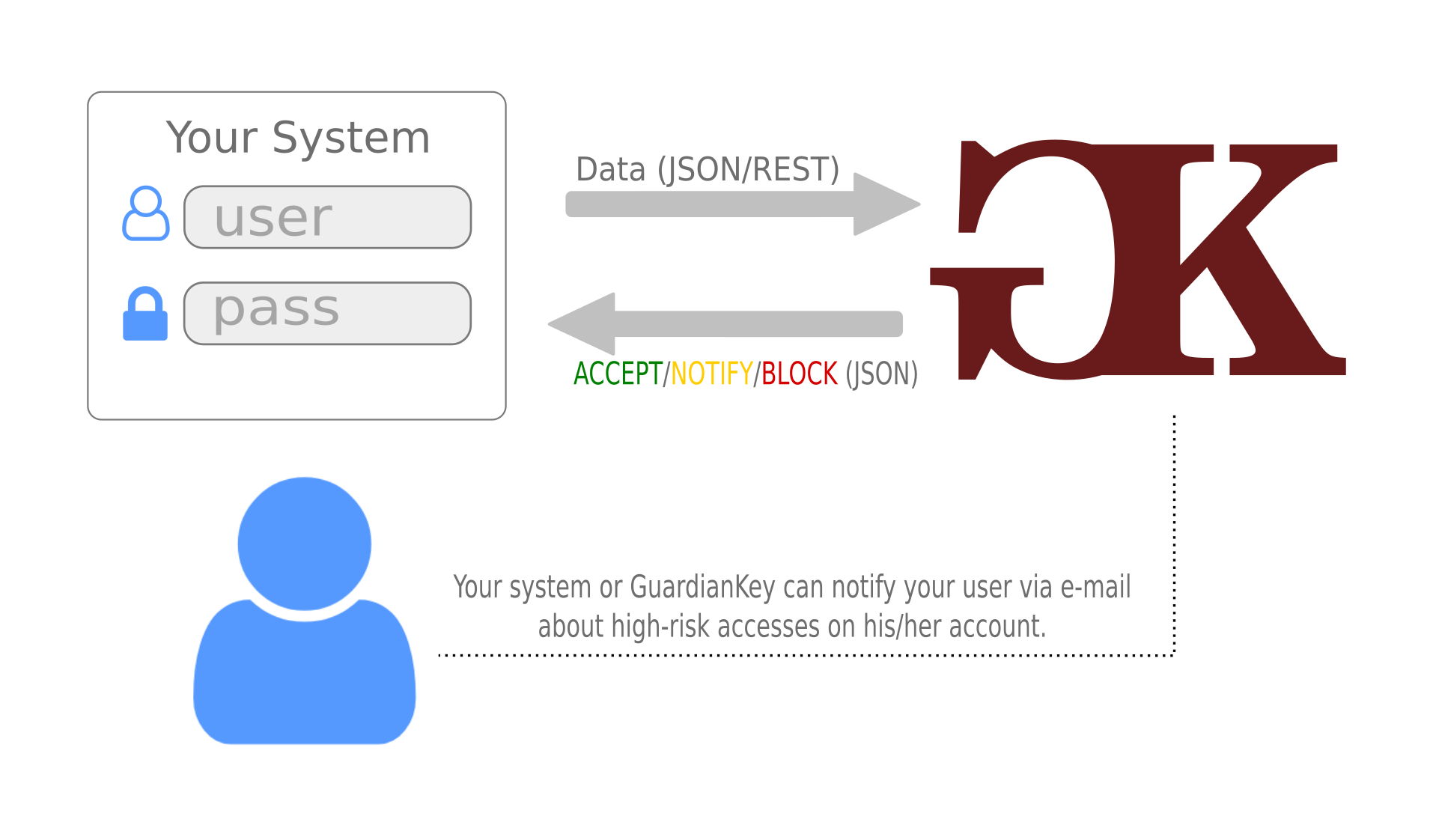
The protected system (your system) sends events via HTTP-REST for the GuardianKey engine on each login attempt.
GuardianKey returns a risk level and a suggested action (ACCEPT, NOTIFY, HARD-NOTIFY, or BLOCK).
Your system or GuardianKey can notify your users about accesses in their accounts. Also, high-risk attempts can be blocked.
Notified users can tell if the attempts were legitimate or not. In the affirmative case, GuardianKey learns for future analysis, otherwise, your security team can be notified.
GuardianKey has a simple API and reference implementations to simplify the integration. Only a few code lines are required to enable the integration. It is also possible to use a reverse proxy, which dismisses coding.
GuardianKey protects your systems against the following threats: Account Takeover, Automated attacks, Brute-force attacks, Anonymization, among others.
Features
No Hardware
Easy deployment
Real time
Transparent
High ROI
High security
Analyzing the results
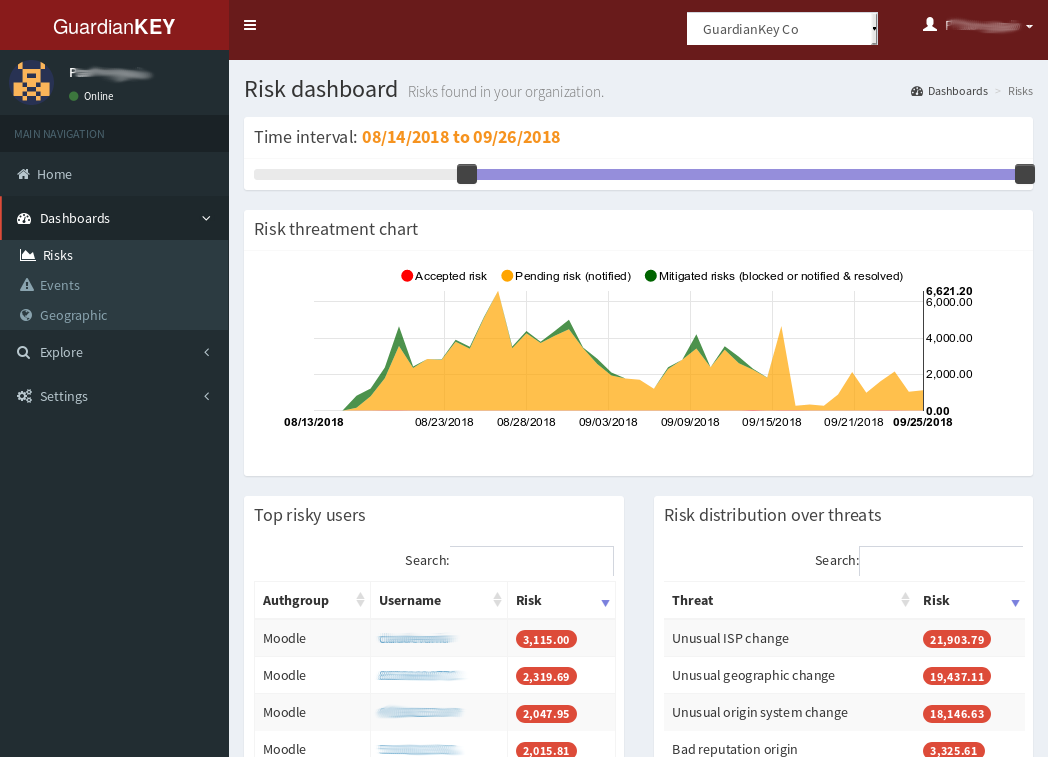
GuardianKey has a panel that enables the administrator to:
-
View logged authentication attempts.
-
Analyze graphs about authentication risks and events.
-
Explore users and events.
-
Set-up policies, authentication groups, notification preferences, etc.
GuardianKey can also send the processed events to a WebHook via REST or directly to your log system (e.g., a SIEM).
See more information about the panel, clicking here.
Resources
- Check our products and services in the site menu
- Video
- Whitepaper
- Documentation for users
- Documentation for developers

